Credit: Aurich Lawson / Ars Technica
In the summer of 2024, corporate anti-malware provider CrowdStrike pushed a broken update to millions of PCs and servers running some version of Microsoft's Windows software, taking down systems that both companies and consumers relied on for air travel, payments, emergency services, and their morning coffee. It was a huge outage, and it caused days and weeks of pain as the world's permanently beleaguered IT workers brought systems back online, in some cases touching each affected PC individually to remove the bad update and get the systems back up and running.
The outage was ultimately CrowdStrike's fault, and in the aftermath of the incident, the company promised a long list of process improvements to keep a bad update like that from going out again. But because the outage affected Windows systems, Microsoft often had shared and sometimes even top billing in mainstream news coverage—another in a string of security-related embarrassments that prompted CEO Satya Nadella and other executives to promise that the company would refocus its efforts on improving the security of its products.
The CrowdStrike crash was possible partly due to how anti-malware software works in Windows. Security vendors and their AV products generally have access to the Windows kernel, the cornerstone of the operating system that sits between your hardware and most user applications. But most user applications don't have kernel access specifically because a buggy app (or one hijacked by malware) with kernel access can bring the entire system down rather than just affecting the app. The bad CrowdStrike update was bad mostly because it was being loaded so early in Windows' boot process that many systems couldn't check for and download CrowdStrike's fix before they crashed.
As part of a wide-ranging security blog post earlier this week, Microsoft announced a seemingly minor change that could have a big impact: "a private preview of the Windows endpoint security platform" that "will allow [endpoint security vendors] to start building their solutions to run outside the Windows kernel."
"This means security products like anti-virus and endpoint protection solutions can run in user mode just as apps do," wrote David Weston, Microsoft's VP of Enterprise and OS Security. "This change will help security developers provide a high level of reliability and easier recovery resulting in less impact on Windows devices in the event of unexpected issues."
This preview will be delivered to companies that participate in Microsoft's Microsoft Virus Initiative (MVI), a list that includes CrowdStrike, Bitdefender, ESET, SentinelOne, Trellix, Trend Micro, and WithSecure. Those companies all have representatives quoted in Microsoft's blog post, all offering some version of (to paraphrase) "security is important and we are pleased to be working with Microsoft to make it better."
Microsoft's language says that security vendors can develop security apps that operate in user mode but not that they must do so. It's not clear whether this announcement is a first step toward booting third-party security companies out of the Windows kernel entirely or if it's simply a new, more foolproof option for companies whose software doesn't need that level of access.
An idea with some baggage
Microsoft's attempts to restrict third-party security companies from accessing the Windows kernel have been contentious in the past. Back in 2006, when Microsoft was simultaneously developing Windows Vista and building the foundation for what would become today's 64-bit editions of Windows, Microsoft wanted to restrict security companies from patching the kernel as they'd been able to in 32-bit editions of Windows, insisting that they do so using more restricted security APIs instead.
But Microsoft was also beginning to offer its own antivirus products at the time, including the first version of Windows Defender. Companies like Symantec argued that restricting their access to the kernel was anti-competitive and that it would give Microsoft's own security products capabilities that third parties couldn't provide.
Working with third-party companies to define these standards and address those companies' concerns seems to be Microsoft's way of trying to avoid that kind of controversy this time around.
"We will continue to collaborate deeply with our MVI partners throughout the private preview," wrote Weston.
Death comes for the blue screen
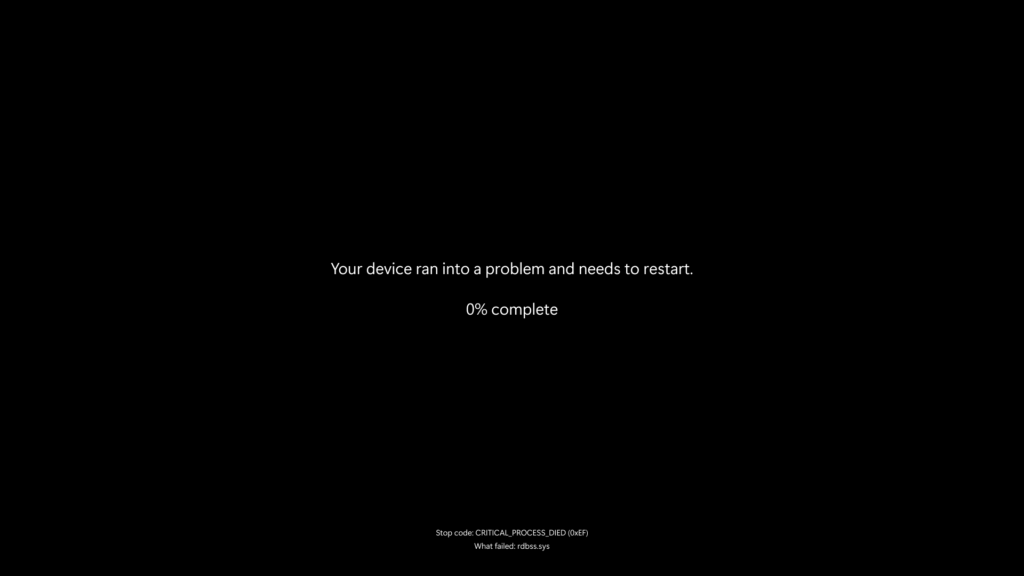
Microsoft is changing the "b" in BSoD, but that's less interesting than the under-the-hood changes.
Credit: Microsoft
Microsoft's post outlines a handful of other security-related Windows tweaks, including some that take alternate routes to preventing more CrowdStrike-esque outages.
Multiple changes are coming for the "unexpected restart screen," the less-derogatory official name for what many Windows users know colloquially as the "blue screen of death." For starters, the screen will now be black instead of blue, a change that Microsoft briefly attempted to make in the early days of Windows 11 but subsequently rolled back.
The unexpected restart screen has been "simplified" in a way that "improves readability and aligns better with Windows 11 design principles, while preserving the technical information on the screen for when it is needed."
But the more meaningful change is under the hood, in the form of a new feature called "quick machine recovery" (QMR).
If a Windows PC has multiple unexpected restarts or gets into a boot loop—as happened to many systems affected by the CrowdStrike bug—the PC will try to boot into Windows RE, a stripped-down recovery environment that offers a handful of diagnostic options and can be used to enter Safe Mode or open the PC's UEFI firmware. QMR will allow Microsoft to "broadly deploy targeted remediations to affected devices via Windows RE," making it possible for some problems to be fixed even if the PCs can't be booted into standard Windows, "quickly getting users to a productive state without requiring complex manual intervention from IT."
QMR will be enabled by default on Windows 11 Home, while the Pro and Enterprise versions will be configurable by IT administrators. The QMR functionality and the black version of the blue screen of death will both be added to Windows 11 24H2 later this summer. Microsoft plans to add additional customization options for QMR "later this year."

-
 C114 Communication Network
C114 Communication Network -
 Communication Home
Communication Home


